Google is the most popular search engine that helps in information gathering & lots of other purposes. Cyber security professionals and cybercriminals both leverage this search engine to do a lot of malicious actions & search lots of different sites and services that reside on the surface web & are crawled by the Google search engine's spider.
One such technique is the use of Google Dorks that we will learn to use in this chapter. This article also talks about a list of well-known Google dorks that ethical hackers and other security professionals use and when they prefer to use these.
What is Google Dorking?
Google Dorking is a technique of hacking wherein the hacker can make advanced searches through specific queries in the search service to identify valuable data on the surface web or content that is hard to find through regular search. Often hackers call this technique Google hacking since they use the Google search engine to do the hack. At the core of this technique the hacker uses explicit modifiers to search queries.
Users can also leverage specific commands like "filetype", "intext", & "site" for getting various detailed search results. Security experts and cybercriminals can use this dorking technique to obtain or extract information about any target system or unauthorized data to exploit security vulnerabilities in apps and websites.
How to use Google Dorks?
It is easy to use Google dorks as we only need to write a dork in Google's search bar and press 'Enter.' There are different Google Dorking commands that help us search for any information on Google. The list of the most commonly used Google Dorks is as follows:
Google Dorks Queries:
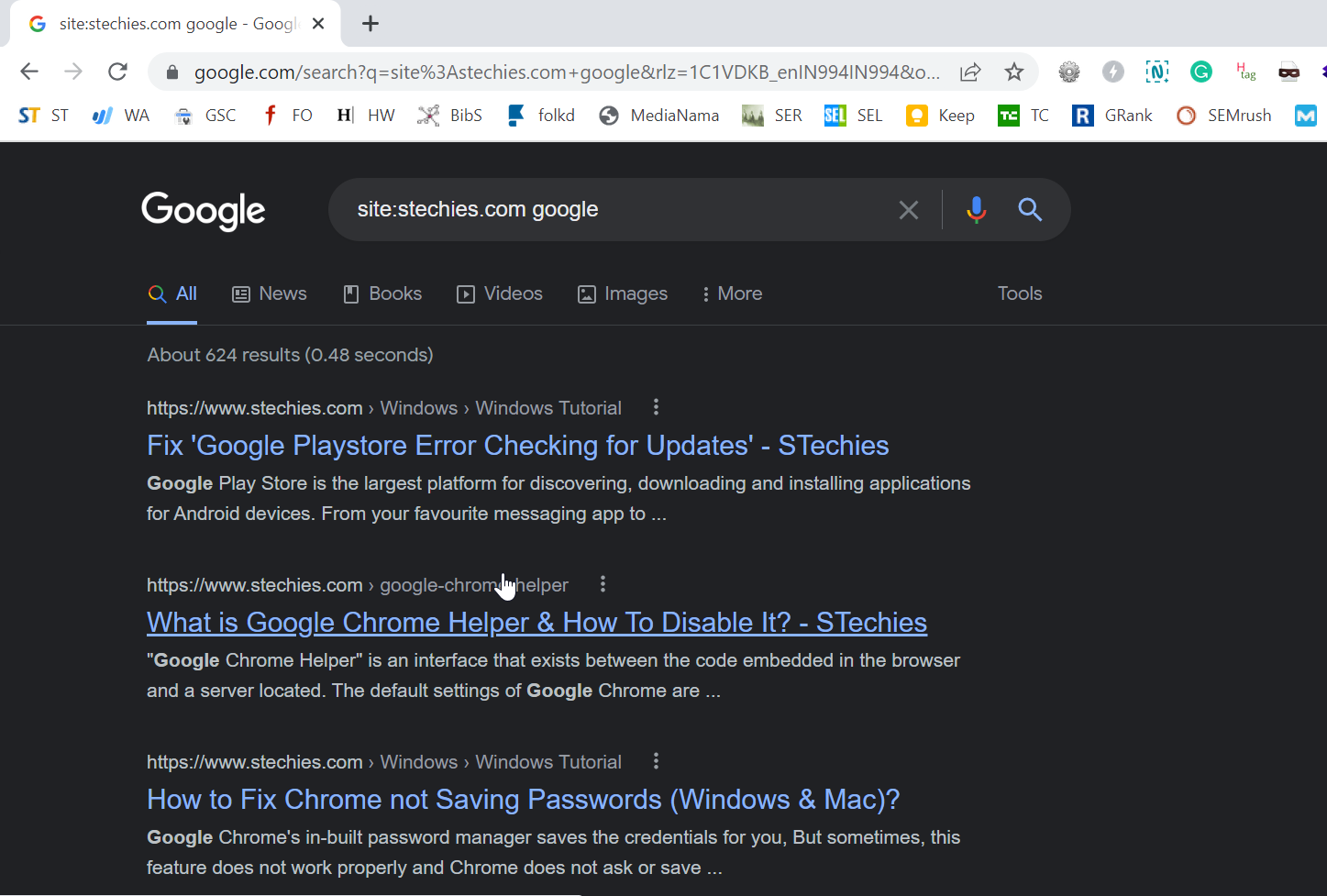
1. site:
"site:" is a command for the Google search engine. It helps search all the websites containing information regarding any specific entity. In the Google search bar, we will type "site:" We can use other Google dorking commands to narrow our search results. Google will restrict the search results to those websites which provide us with the required information.
At this, we can take an example to know how this command works. Let us say a person wants to buy an android phone and is searching for a mobile phone, which is introduced later in 2022.
After getting a list from the search results, he reviewed the pages and found that Xiaomi Redmi 10 2022, Realme Q5 Pro, Samsung Galaxy A13, etc., are mostly preferred. His next step would be to collect more relevant information about these mobile phone brands from genuine websites. Here, the "site:" Google command will come into action. It will help him find the most relevant and accurate information by narrowing down the search to some specific websites only.
Let us take one more example of this Google Dorking command "help site:www.google.com," which will search for pages specifically about help in www.google.com. Also, the "help site: com" will search for pages about help service in ".com urls."
Important Note: We need to write the "site:" and the domain name without any space between them, or it will not work.
Syntax:
site:domainname or site:https//domainname/
2. filetype:
Filetype is one of the popular fundamentals of Google Dorking. It helps to separate a large number of files. With the help of this command, we can easily find the pdf, jpeg, gif, etc., Google files. It can also filter log files for us.
Log files are advantageous for collecting information associated with an organization because these are the files that maintain records of all the events that take place in an organization. We need to write the command mentioned below in the search bar to access the simple log files.
Syntax:
filetype:log
It will provide us with all types of log files. But this will not be of great help as long as we try to narrow down our search using specific filters.3.
3. intext and allintext:
We can use this command to find any specific text within the search result of the web pages. Generally, we can use the "intext:" in two ways. The first is we can get a single keyword in the search results and the second method is to obtain multiple keywords in the search.
For the first method, the syntax for the "intext:" command is:
intext:usernames
In the second method, we can use the "allintext:" command in place of "intext:" and separate the keywords using a single space. If we type and enter the "allintext" in the search bar, Google will add all the relevant pages in the search result with the keywords mentioned in the query. For this reason, we need to write these commands with appropriate keywords so that our search results do not lack the essential information.
Suppose we want to search for some web pages containing information related to usernames and passwords, and then we will write the query as follows:
allintext:"username" "password"
Syntax:
intext:domainname or allintext:domainname
4. ext:
When we need to find out the documents of specific type, we can use the "ext:" dork. Ext is a command that we use to define file extensions. It functions like a "filetype:" command. For example: site:https://www.google.com/ ext:pdf
Google Search Operators:
1. cache:
Google records both the current and previous versions of web pages in its cache, and sometimes these pages can provide us with a lot of information about the various domains like technical, educational, and others. It also reveals information initially used for testing pursuits only, which were removed later in the later versions but are still available in these versions, which we can access through Google's cache.
The "cache:www.google.com web" will display the cached content with the term "web" highlighted. We can also access this functionality of Google by clicking on the "Cached" link on Google's main page with the search results. The query "cache:" will provide the version of the web page Google stored in its cache.
Syntax:
for finding out Google's cache on the Google homepage
cache:www.google.com
2. link:
This command helps find the list of all the relevant web pages that have links indicating the Facebook homepage.
Syntax:
link:www.facebook.com
3. info:
Using this Google dork query, we can get the relevant information about the domain name we will search for in the search bar.
Syntax:
info:www.twitter.com
4. inurl and allinurl:
If we type "inurl:" in our query and press enter, Google will limit the results to documents having that word in the URL. For example, "inurl:facebook search" will provide those documents that mention the word "facebook" in their URL and cite the term "search" anywhere in those documents (URL). If we put "inurl:" before every word in the command is the same as when we put "allinurl:" at the front of this command. It means "inurl:facebook inurl:search" is the same as "allinurl: google search."
Syntax:
inurl:domainname inurl:search
allinurl:domainname search
5. intitle and allintitle:
The intitle is a command which we use when we need to separate the documents depending on the titles of HTML pages. The HTML pages contain those keywords in their title that describes the whole document. We can specifically use this Google Dork query to get what we want.
If we add "intitle:" in our query, Google will limit the results to documents having that word (words which we will use after the Google Dork query) in the title. When we put "intitle:" before every word in the command is the same as when we put "allintitle:" at the front of this command. It means "intitle:facebook intitle:search" is the same as "allintitle: google search."
The query "intitle:google search" will return documents that explicitly cite the word "facebook" in their title and mention the term "search" anywhere in those documents (URL).
Syntax:
intitle:domainname inurl:search
allintitle:domainname search
6. define:
The query "define:" will provide us with definitions of those terms we enter after the query, collected from different online references. This definition will have all the terms in the exact order we typed them, i.e., the result will be for the whole phrase entered.
Syntax:
define:cybercriminals
7. stocks:
Google treats other queries as stock ticker symbols when using the "stocks:" query. It will link to those web pages having stock information for those symbols. For example, "stocks:GOOGL" will show information about Google.
Note: We need to type the ticker symbol of the domain, not the company name.
Syntax:
stocks:ticker symbol of any domain
stocks:GOOGL
How to access online cameras using Google Dorks?
We can access live camera web pages that do not have IP to restrict using Google hacking techniques. If a person is creative enough to work with Google Dork, they can also take control of the entire admin panel remotely. Even they can re-configure the cameras as they want to.
Syntax:
intitle:webcamXP 5
inurl:top.htm inurl:currenttime
inurl:"lvappl.htm"
When we use the "top.htm" in the URL with the current date and time, we can fetch the list of live cameras that are publicly exposed.
Dork Command using Multiple Google Dorks:
We can use different Google Dorks individually, whereas we can also use more than one dork at a time. It is known as composing multiple Google Dorks. Suppose we can use the "intitle:" query with "filetype:" It will filter out all the documents that contain the title and mentioned file format. For example, intitle:google filetype:pdf where Google will restrict the search result with documents satisfying the above queries.
We can also add other Google Dorks when we need further information, such as "allintext:" with "filetype:"
How to Explore LOG files for Login Credentials?
We can use this technique to find the .LOG files accidentally disclosed on the internet. It is generally a LOG file having indications about what the credentials of any system might be or information regarding various admin or user accounts that are present in the system.
Syntax:
allintext:password filetype:log after:2021
How to Explore Open FTP Servers?
There are several reasons behind the cause of the internal information of the FTP (File Transfer Protocol) getting published unintentionally. It is because of the absence of setting access permissions in the FTP. We will be able to readily explore the publicly disclosed FTP Servers using the following dork command, which can also help to explore many other relevant pieces of information.
Syntax:
intitle:"index of" inurl:ftp
intitle:"index of" inurl:http after:2021
intitle:"forum" inurl:http after:2021
Google Dorks for Hacking Purposes:
The cybercriminals and attackers who wish to search by a domain other than the URL can use the advantage of Google dork queries. The list of the Google Dorks for hacking purposes is as follows:intitle:
- intext:
- inurl:
- site:
- define:
- info:
- link:
- maps:
- book:
- weather:
- movie:
- phonebook:
- related:
Conclusion:
The objective of using Google Dorks should be to use these dork commands and tricks to make others and ourselves secure. It is the responsibility of every citizen to use and fetch the information for security purposes. If you have read this article, it indicates that you should leverage these techniques to a certain extent in cyber security.