The AS Java system gives an error message- "Issuer of SSO ticket is not authorized" when a login attempt is made to the backend ABAP system utilizing a Logon Ticket. A single Sign-On (SSO) has been created set-up between an ABAP Backend System and an AS Java frontend system.
The issue can also take place when there is a JCo connection made from Java to ABAP systems and SAP Logon Ticket is utilized for authentication related purposes.
Regenerating the error
- Attempt SSO authentication from AS Java (frontend) system to ABAP (backend) system.
SOLUTION
Two major steps of SSO configuration occur between the Ticket Issuing AS Java System and the Ticket Accepting ABAP Backend System. The exception message (Issuer of SSO ticket is unauthorized) can be reflected in any of the configuration steps is not done in a proper manner.
A Public Key Certificate of the AS Java System is uploaded to ABAP Backend System under STRUSTSSO2 transaction. The ABAP system utilizes this Certificate for decrypting the incoming MYSAPSSO2 cookies from the AS Java System. In case, the public key certificate is not present in the ACL, the exception message is then displayed.
An entry of the AS Java system is required to be maintained in the ACL (Access Control List) of ABAP system under transaction STRUSTSSO2. The ABAP system maps reflect all the details of all incoming MYSAPSSO2 cookies against the entries done in the ACL. If it does not find a matching entry (correct SID-Client combination) then it reflects an exception message.
Please follow the steps below in order to resolve this issue:
1. On the ABAP Backend System, user goes to transaction STRUSTSSO2 and verifies under Certificate List whether a Certificate of AS Java System is available or not.
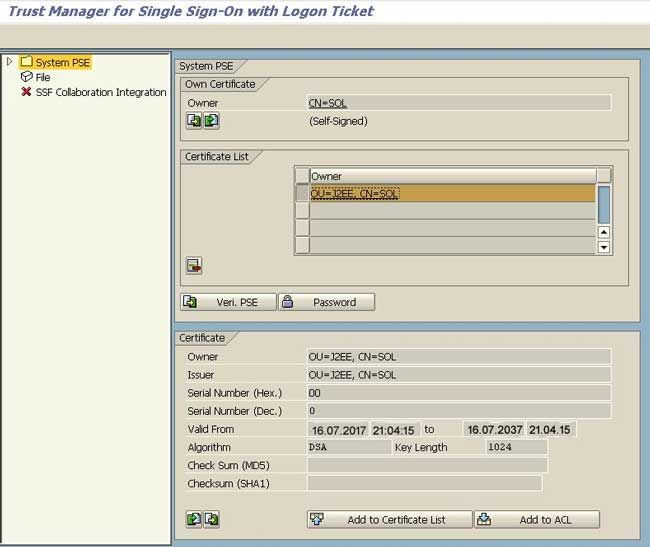
A user makes sure that it is created utilizing the DSA Algorithm and is valid. A user must also ensure that the Certificate has been added in ACL list as well as in the certificate list.
2. On ABAP backend System, user goes to transaction STRUSTSSO2 and ensures that a valid entry for AS Java system is present under the ACL list. SID value should ideally match the SID of the AS Java System (Ticket Issuing System). The Client value should also match the UME parameter logon.ticket_client value in AS Java System (Ticket Issuing System).
Important: The system ID and client combination should be unique once the tickets are about to be accepted by an ABAP system. Therefore, the user must change the default client for the J2EE Engine (000) to a client which doesn’t exist on the ABAP system (for e.g. 999 in an Add-In installation, where the system IDs are the same.
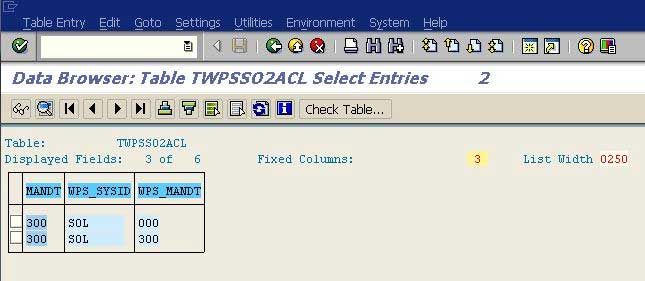
3. On ABAP backend System, user should go to transaction SE16 and access the table TWPSSO2ACL. A user must make sure that no invalid entries exist in the table. Incase, there are any invalid entries are present, then those should be deleted. Also, make sure that a relevant ACL entry for AS Java system is present in the table TWPSSO2ACL.
4. If everything is fine, then for a failed SSO attempt, user should capture SM50 traces in ABAP system and web-diagtool trace in AS Java system. The steps are listed below:
I) in the ticket accepting system (ABAP), setting up the security trace level.
- Calling the transaction SM50 (process list):
- Process -> Trace -> Reset -> Workprocess Files
- Key combination: F5 (select all), CTRL+Shift+F7 => Dialog box;
- Set trace level=3 and check the "Security" component.
If required, user should repeat these steps again for each server (see transaction SM51), unless he is able to use a specific server for reproducing the error (for example, by excluding the load distribution).
II) Download and install the latest free version of HTTPWatch Tool Basic Edition from http://www.httpwatch.com/download/.
III) For NW 7.2 and above systems, a user should Run the Troubleshooting Wizard with log locations as per example 3 of sap note 1332726. For NW 6.40 To NW 7.1 versions, Run the Web-diagtool with log locations as per example 3 of sap note 1045019, for a detailed step by step description please refer to SAP Document 2563258.
IV) User should Open another browser and go to Tools -> HTTPWatch Basic -> Press 'Record' -> reproduce a failed SSO to the backend system.
V) When the SSO fails, user should wait for a minute and then press 'Stop' on web-diagtool /troubleshooting wizard console and HTTPWatch Tool so that the resulting traces are picked up.
VI) Attach the HTML web-diagtool/troubleshooting wizard log, SM50 trace and HTTPWatch trace to the message.
VII) A user must Specify the time at which he reproduced the issue and the UserID involved.